Hi!
Setup: macOS with virtualization software, usb automount disabled.
Nitrokey Storage 2 64GB, App(Image) 1.4, FW 0.54, checksums firmware match. Not flashed. AppImage 1.3.2 doesnt work, AppImage 1.4 checksum matches.
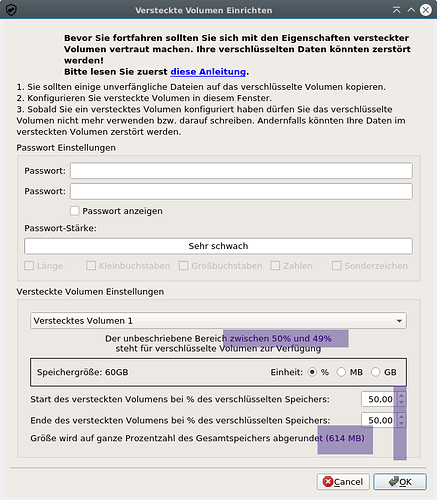
I played around with that stick and configured it. I wanted to initiate the hidden volume.
- Created gpt partition table inside the encrypted area after unlocking
- Created unformated partition with gparted
- used LUKS and ext2 (FAT doesnt change the problem anymore).
- Tried some reformats and repartitioning.
AppImage 1.4 under debian Linux VM now says that I can configure a hidden volume between 49 and 50% (600MB only). There was no data written to the encrypted disk(s) except the file system/LUKS information.
Steps I tried to solve the problem:
AppImage Admin or normal mode
-reset to factory defaults
-reinit drive
-destroyed encrypted data (new AES key generation)
-filled drive multiple times with random data by AppImage fuction (special)
-gpg card erase like your website lists
Unecnrypted Storage doesnt get clean (not even if I choose factory defaults?!)
AppImage always says encrypted storage is full. Setting proper values not possible anymore (maybe wasnt possible anytime).
Stick is new, except filling with data/deletion not used the storage.
Any ideas what I can do? I want to use LUKS encrypted hidden volume in encrypted LUKS volume inside encrypted Nitrokey storage. I am not paranoid. Definitly not. I am not. Believe me.
Thank you for your support.
Best regards
NitrokeyTester