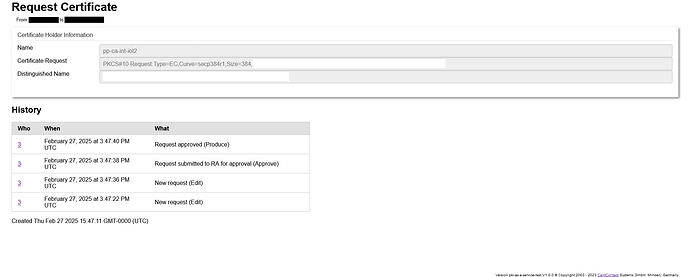
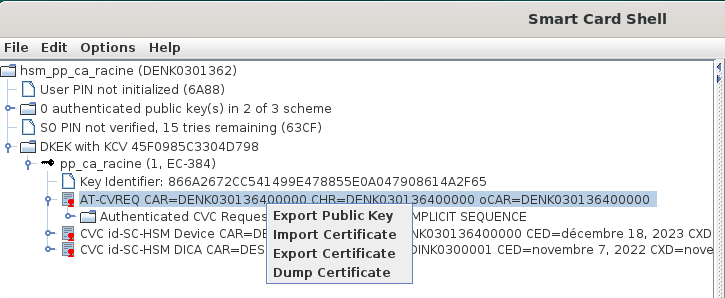
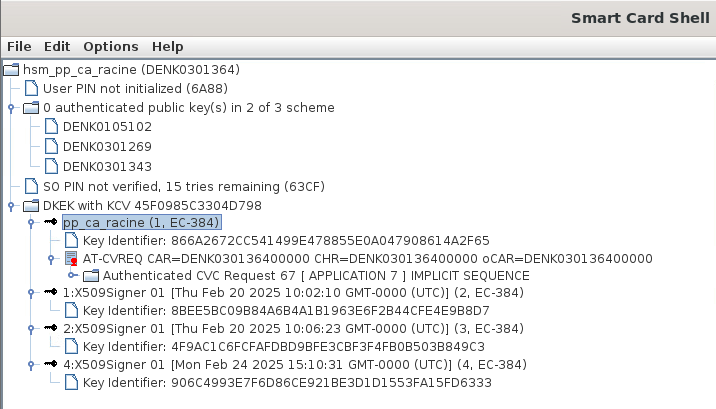
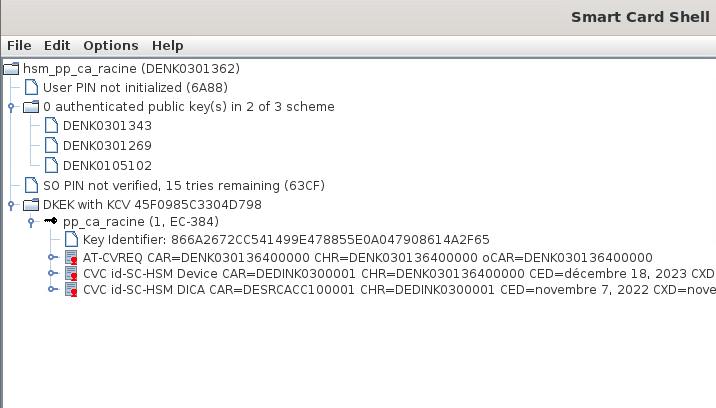
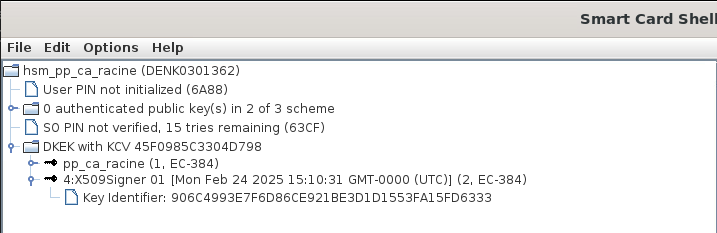
My CA is stored on a Nitrokey HSM2 which requires m-of-n authentication, using other HSM2.
In order to protect from device failure or loss, I would like to:
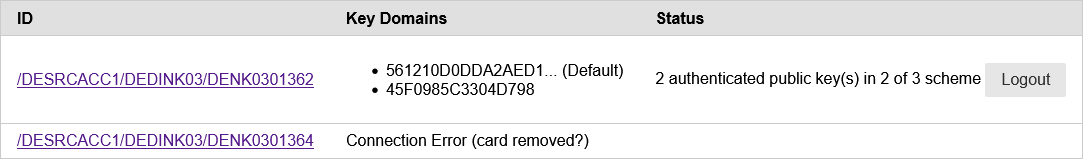
- be able to use the CA with a secondary CA HSM, identical to the first one
- give my colleagues the ability to use PKIAAS with their own personnal HSM
For the first goal, I used SmartCard Shell to import both DKEK and private key on my secondary HSM. I wonder if there are any more necessary step required in PKIAAS though.
For the second goal, I did the procedure below.
Steps to reproduce
I registered my personal HSM to my self-hosted PKIAAS instance. In order to give my colleagues the ability to use PKIAAS, I did the following:
- went to “Home”
- clicked on "Create TrustCenter Subject (Trust Center)
- plug a personnal token to authorize
- click on “Add Token”
Then I log out of PKIAAS.
Expected results
My colleagues are able to connect to PKIAAS with their own HSM.
Actual results
Colleagues are asked for their PIN, and after successful authentication they got the following error:
How could I reach both of my goals?