HOWTO: KEY CREATION / SSH / FIDO2
Make sure nitropy works as intended. If that is the case yo can use the following script with key-name as only argument:
#!/usr/bin/env bash
set -uo pipefail
name="$1"
ssh-keygen \
-t ed25519-sk \
-O resident \
-O verify-required \
-O "application=ssh:$name" \
-f "$HOME/.ssh/id_ed25519_sk_nk3_$name" \
-C "nk3_$name"
- omit
residentif you do not want to have the “key stub” stored on the nitrokey - this is more secure but less convenient as you can not usessh-keygen -Kto create a local copy of the stub. - you can symlink the 2 created files to
id_ed25519_sk/id_ed25519_sk.pub, use ssh with the-iflag or useIdentityFile ~/.ssh/id_ed25519_sk_nk3_<name>in~/.ssh/config - to check the correct creation of the slot on the stick call
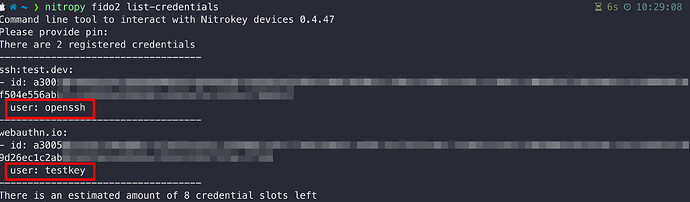
nitropy fido2 list-credentials