I’m trying to import an existing key into a Nitrokey HSM 2.
It appears the PKCS11 interface does not implement C_WrapKey and C_UnwrapKey
I’ve not been successful importing a PKCS#12 container.
I’ve tried the methodology discussed in other threads here, using openssl to convert my keys into a p12 container:
If I generate a test key and convert to a PKCS#12 container as follows:
openssl genrsa -f4 2048 >test0.pem
openssl req -new -x509 -key test0.pem -out test_cert.pem -days 9999 -subj "/C=US/ST=California/L=SanJose/O=cfrantz/CN=project"
openssl pkcs12 -export -out test_cert.p12 -inkey test0.pem -in test_cert.pem --passout pass:abc123
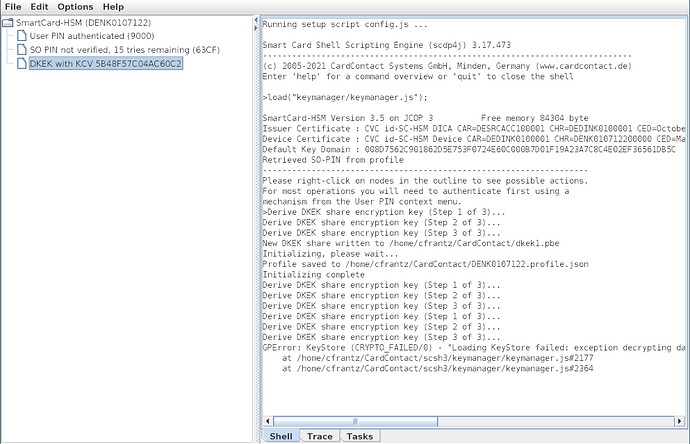
And then try to import test_cert.p12 via the Smart Cart Shell, the shell always responds with:
Derive DKEK share encryption key (Step 1 of 3)...
Derive DKEK share encryption key (Step 2 of 3)...
Derive DKEK share encryption key (Step 3 of 3)...
GPError: KeyStore (CRYPTO_FAILED/0) - "Loading KeyStore failed: exception decrypting data - javax.crypto.BadPaddingException: pad block corrupted" in /home/cfrantz/CardContact/scsh3/keymanager/keymanager.js#2177
at /home/cfrantz/CardContact/scsh3/keymanager/keymanager.js#2177
at /home/cfrantz/CardContact/scsh3/keymanager/keymanager.js#2364
I’m using OpenSSL 3.0.7 and scsh3.17.584. What am I doing wrong?
Best,
saper
March 28, 2023, 8:59am
2
Looking at https://docs.nitrokey.com/hsm/mac/import-keys-certs.html
Did you import your DKEK share? Can you show us if the DKEK has been imported correctly?
I’ve followed the instruction on the linked page. Afterwards my device shows DKEK with KCV <hex> (It also did before, but I redid the procedure just in case I’d made a mistake).
However, I’m still unable to import my PKCS#12 container (same failure message).
I’ve attached my test keys & certificate (this key is for testing only. I intend to discard it after debugging this issue).test_keys_and_cert.zip (5.2 KB)
Thanks for your help,
sc-hsm
March 30, 2023, 10:49am
4
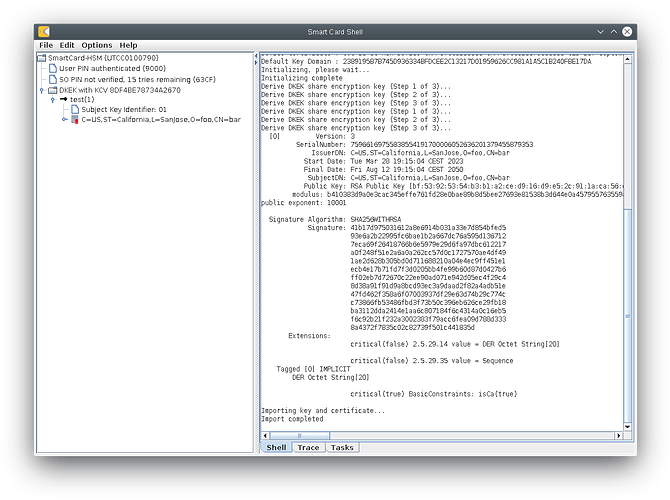
Tried that myself and it worked as expected:
Can you try the following command in the Smart Card Shell:
>var p12 = new KeyStore("BC", "PKCS12", "test_cert.p12", "abc123");
What Java version are you using ? Mine is Java 11.
I’m using my system’s default install of java:
$ java --version
openjdk 17.0.6 2023-01-17
OpenJDK Runtime Environment (build 17.0.6+10-Debian-1)
OpenJDK 64-Bit Server VM (build 17.0.6+10-Debian-1, mixed mode, sharing)
I get the same error when I create the KeyStore object at the shell.
I installed jdk 11 from jdk.java.net . After re-arranging the scsh3gui invocation a bit, I’m able to import my test PKCS12 container.
$HOME/jdk-11/bin/java \
-Dorg.bouncycastle.asn1.allow_unsafe_integer=true \
-Djava.library.path=./lib \
-Dsun.security.smartcardio.library=/lib/x86_64-linux-gnu/libpcsclite.so \
-classpath 'lib/*' \
de.cardcontact.scdp.scsh3.GUIShell
Thanks again for your assistance.
For what it’s worth, I tried several versions of the java jdk from jdk.java.net .
The KeyStore loading command posted above appears to work on jdks 11-16. It fails on jdks 17 and beyond, always complaining about corrupted padding:
>var p12 = new KeyStore("BC", "PKCS12", "test_cert/test_cert.p12", "abc123");
GPError: KeyStore (CRYPTO_FAILED/0) - "Loading KeyStore failed: exception decrypting data - javax.crypto.BadPaddingException: pad block corrupted" in shell#0
Considering the failure happens with the official JDK releases, I don’t think the problem is related to Debian’s particular build/packaging of Java.
saper
April 2, 2023, 12:24am
7
Standard Sun crypto provider has no issues reading your PKCS#12 file:
$ /usr/local/openjdk17/bin/java -version
openjdk version "17.0.6" 2023-01-17
OpenJDK Runtime Environment (build 17.0.6+10-1)
OpenJDK 64-Bit Server VM (build 17.0.6+10-1, mixed mode, sharing)
$ /usr/local/openjdk17/bin/keytool -list -providername SUN -storetype PKCS12 -storepass abc123 -keystore test_cert.p12 -v
Keystore type: PKCS12
Keystore provider: SUN
Your keystore contains 1 entry
Alias name: 1
Creation date: 2 kwi 2023
Entry type: PrivateKeyEntry
Certificate chain length: 1
Certificate[1]:
Owner: CN=bar, O=foo, L=SanJose, ST=California, C=US
Issuer: CN=bar, O=foo, L=SanJose, ST=California, C=US
Serial number: d4e70dc810558b38b4bb353f279c279b824c8b9
Valid from: Tue Mar 28 19:15:04 CEST 2023 until: Fri Aug 12 19:15:04 CEST 2050
Certificate fingerprints:
SHA1: 49:84:0A:4C:6F:65:80:CD:6D:83:8C:AC:BF:1A:E5:83:9C:B8:0C:33
SHA256: 44:91:10:AE:79:94:F3:A8:DA:E0:FD:C6:74:6F:3B:F8:36:22:E8:57:39:FA:C5:80:78:30:25:05:C6:31:1E:70
Signature algorithm name: SHA256withRSA
Subject Public Key Algorithm: 2048-bit RSA key
Version: 3
Extensions:
#1: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: B6 46 3C 37 27 77 66 4B 8A B0 28 C3 79 A8 33 73 .F<7'wfK..(.y.3s
0010: FE 6B 92 C5 .k..
]
]
#2: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen: no limit
]
#3: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: B6 46 3C 37 27 77 66 4B 8A B0 28 C3 79 A8 33 73 .F<7'wfK..(.y.3s
0010: FE 6B 92 C5 .k..
]
]
*******************************************
*******************************************
The issue might be with the Bouncy Castle provider…
saper
April 2, 2023, 12:51am
8
Confirmed, this is BC provider fails to load certain P12 keystores under Java 17 (pad block corrupted) · Issue #1018 · bcgit/bc-java · GitHub fixed in BouncyCastle release 1.70.
I have removed bcpkix-jdk15on-1.67.jar and vcprov-jdk15on-1.67.jar from the lib/ directory and replaced them with the newest release:
https://bouncycastle.org/download/bcprov-jdk18on-172.jar https://bouncycastle.org/download/bcutil-jdk18on-172.jar https://bouncycastle.org/download/bcpkix-jdk18on-172.jar
The SHA-256 of the files:
56a054cb170d41fb1f8ba0b29568806258b7ffefdc5e98b77ef96d4740f3d6bc bcpkix-jdk18on-172.jar
39287f2208a753db419f5ca529d6c80f094614aa74d790331126b3c9c6b85fda bcprov-jdk18on-172.jar
45377fdb6560a971eea725f507d91fd6b8fbd0797d61bfc86f2cb653c58186a4 bcutil-jdk18on-172.jar
Opening of your PKCS#12 file works for me now with OpenJDK 17 and the BC provider under scsh3.
sc-hsm
April 5, 2023, 2:00pm
9
Fixed in Smart Card Shell 3.17.587, available at www.openscdp.org .
1 Like