I have got the error message from Nitrokey HSM when “2.in” file(4,158 bytes) is signed using EC key. Please see the attached below.
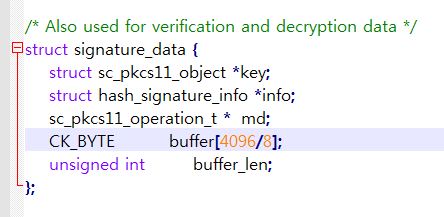
To solve this problem, I think that OpenSC library should be revised for the buffer size which is in the “signature_data” structure in “mechanism.c” in OpenSC. Am I correct?
However, I am not familiar with Linux and Git-Hub environment so, can anyone let me know how to build OpenSC locally in Linux if I am correct ? I am using Ubuntu 16.04 on Virtualbox. If I am wrong, please let me know how to solve this problem.
I have downloaded the latest OpenSC source.
The latest OpenSC version is 0.15.0, Ubuntu 16.04.
I got hints from the website below; OpenSC compiling can be done according to this.
I will try the followings tommorrow.
- Download OpenSC 0.15.0.
- Revise source code for increasing buffer size
- Build according to the OpenSC wiki above.
Hi!
Perhaps newer OpenSC will deal with this. Please take a look at our prebuilt OpenSC v0.18 packages on Github: opensc-build. Along with the packages there is also a built script (OpenSC-build.sh), if you would like to build it locally.
Thank you very much. I will try and share the result.
I got a same error result after using opensc-build.
In additon, I have revised source code and have re-builded it.
However, I got another error codes as follows.
The signature buffer size of “signature_data” structure is increased.
The input buffer size of “sign_data” function is increased.
By the way, I am using “pkcs11-tool --module /usr/lib/pkcs11/opensc-pkcs11.so” for signing data. Is there another option ? for example, using openssl engine.
I am looking forward to any reply. Thank you.
I see. I think this is an OpenSC issue indeed. I just have found, that they might not support ECC through PKCS#11 interface - see Github issue. Lately there were some changes for PKCS#15 in that matter (not released yet). If you would like to, you can ask directly on the project’s issue site, when it will be supported for your use case. In that case please link it here.
Thank you for your reply. I have submitted an issue ticket at OpenSC.
As you mentioned, I think that there is no ECDSA direct interface including message digest, eg sha256 ; just raw signature.
I need to do sha256 first and then sign the hash value. I had forgot to consider the message digest for signature generation.
Thank you for your support again.
1 Like
