Hi,
My experience so far with Nitrokey Pro has been miserable. It arrived very late via very expensive courier and is proving to be a pain to work with. Forgive my unhappiness.
Please can someone help me or point out my ignorance? That will be very much appreciated.
I want to use both GPG and a X509 cert on the Pro, the site says it is possible:
" Encrypt your emails with GnuPG, OpenPGP, S/MIME or your favourite email client. Keep your secret keys secure on your Nitrokey."
A user says:
“The same RSA keys are used for GnuPG/OpenPGP and S/MIME/X.509. Basically you should generate the OpenPGP keys first and afterwards generate a X.509 certificate for one of the keys. There is space reserved for one X.509 certificate. So you would end up with 3 x RSA keys and 1 x X.509 certificate.”
Jan says:
“Nitrokey Pro has space for 3 RSA keys (encryption, signing, authentication) and one X.509 certificate. RSA keys can be used for both OpenPGP and X.509/PKCS#11. Now, for your existing key you should generate a Certificate Signing Request and send it to your CA. You can store the returned X.509 certificate into your Nitrokey Pro.”
I see many complaints online about poor documentation and the documentation that is there is either incomplete or confusing. Where is the official documentation to do the above? Manual? PDF?
I followed How to generate certificate signing request? and managed to generate the keys, generate a CSR from the no.3 auth key, have it signed by our CA and import the DER cert into the Pro.
I tried importing a .p12 file but that failed with many errors.
So I have “3 x RSA keys and 1 x X.509 certificate”. Using GPG card edit I see the keys.
I only know how using this command: “readcert 3 >mycert.der” to see that the DER cert was imported into the Pro. How else can one show the X509 cert on the Pro?
So, if I understand it correctly, the no. 3 key is for auth and that private RSA key was used to generate the CSR and hence makes up one half of the key pair, the other half is the X509 cert.
I can use gpg-agent to load the auth key and SSH to hosts. Good.
I now turned to the TLS cert auth using X509 cert in browser.
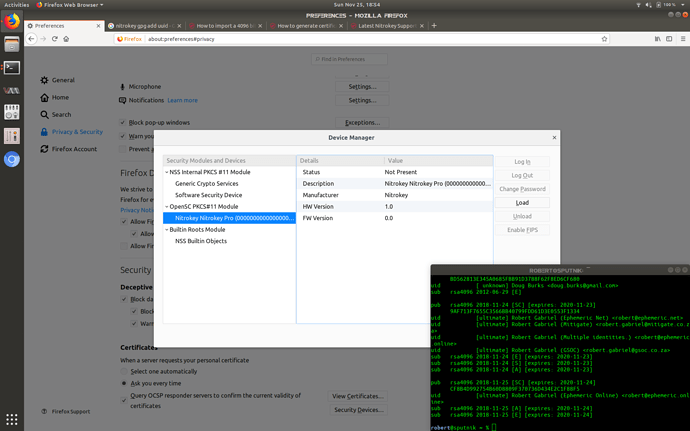
Firefox and Chromium both see the Pro as “Not present”. I have installed the PKCs11 module in both browsers and they recognise the Pro but that’s it. I cannot login to the Pro from Firefox.
I have attached a screenshot from Firefox.
I’m using Ubuntu 18.04 which means recent versions of GPG, OpenSC etc.
What have I missed or done wrong?
Thank you.