Hello,
I want to re-register my 2 keys on all services I have signed up and I was wondering if I can hit any limits doing so.
Also is it possible to list all places I have used the key?
Hello,
I want to re-register my 2 keys on all services I have signed up and I was wondering if I can hit any limits doing so.
Also is it possible to list all places I have used the key?
Hey @Browse1236
you did not mention which Nitrokey you use, thus I am assuming Nitrokey 3, but the information should widely be the same for Nitrokey FIDO2 devices. I’ll be making this short (and trivialized), please check the linked article at the end for more details.
Generally there are 2 ways to store credentials on (NK3s) FIDO2 devices:
Most services use 1), these cannot be listed and basically there are unlimited of these to be kept on the Nitrokey 3 as the credentials are “derived” from a unique “secret” (Attention: simplified, but roughly that’s it)
For the Resident Keys 2) this looks different, you can e.g., list them (e.g., through: chrome://settings/securityKeys ) Sign-in data and there is an upper limit how many of these can be stored (currently 20) …
You can try out both methods using webauthn.io by opening “advanced settings” and switching of the respective drop-downs to “discouraged” (for discoverable credentials).
So generally I would highly recommend to have at least 2 devices registered with any service, usually you will never hit a limit doing so.
I would also recommend to read FIDO2, WebAuthn, Passkeys in 2022 and 2023 | Nitrokey - it comes with some more background information.
best
Thanks for the reply!
Now I understand that most services I use don’t support fido2 ![]() .
.
I also tested authentication in both Chromium (Ungoogled Chromium and Brave) and Firefox browsers. Unfortunately FF doesn’t ask for PIN while using fido2. It also doesn’t activate the key while using fido2. I guess it doesn’t support it…
The last thing I tested is OpenSSH. Using the terminal, it doesn’t ask me for PIN. Which is pretty strange since I see OpenSSH entry in sign-in data
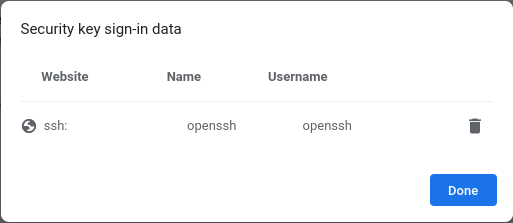
This lets me believe that OpenSSH is using fido2 and every time I use it I should be asked for a PIN. Am I doing something wrong?
Last thing: on the topic of ssh, should I copy the private and public key data on every device I am using or I can “extract” them from the key?
hey hey,
Only the most recent Firefox versions fully support FIDO2 (and thus PIN verification), see: https://hg.mozilla.org/mozilla-central/rev/5d01d24be048 (technically we are talking about CTAP2 support)
For me using the (resident) key created like this:
ssh-keygen -t ed25519-sk -Oresident -Oapplication=ssh:my_servername -f /tmp/my_servername
requires a user presence check (touching the device) and not a pin. But the Nitrokey 3 has to be inserted, otherwise using the identity for logging in via ssh will not work.
If you choose to use ssh-resident keys, you can always extract (and use them) on any machine by calling:
ssh-keygen -K
which will require you to input the pin. (So if someone steals your Nitrokey 3, they need your pin to extract/use the ssh-keys).
So far I know you can also skip creating a file by using ssh-agent, then it should be possible to add the ssh-key using ssh-add -K, but no own experience here as I don’t use ssh-agent.
best