Trying to set up OTP as TOTP token in Mailbox.org, web interface.
To tell the truth I am very frustrated. It seems, since all howto’s are different and, to be honest quite unclear, and nearly all use smartphones (which I do not possess), that this kind of authentication is not really promoted.
In Mailbox.org you get the following
As you see, it gives you the possibility to generate the token.
If you do you get: (e.g. 8bit, sha512, 60sec)
which should give me what I need by clicking on the link? Or by using seed? No idea, no understanding at all!
So if you take the seed and put it in the app where there is written secret key, that gives: too long for this device. Either this is too long (what is short enough then?) or it is wrong to do so. No understanding. No explanation on the web that i have found.
Now if you instead click on the link, in firefox you get a generic oops cannot execute.
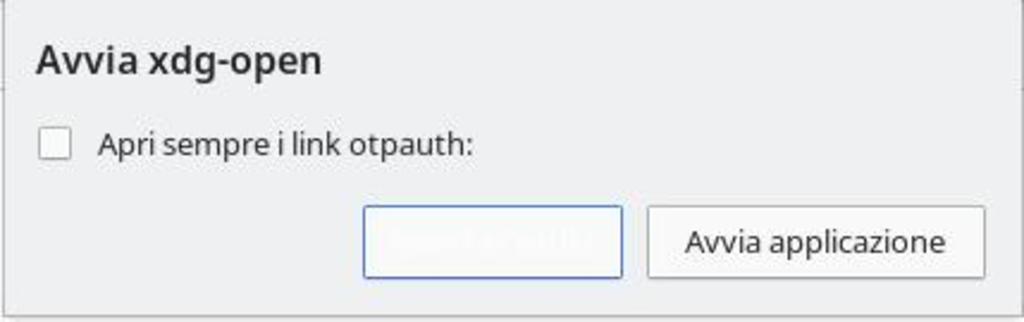
In opera you get a better error:
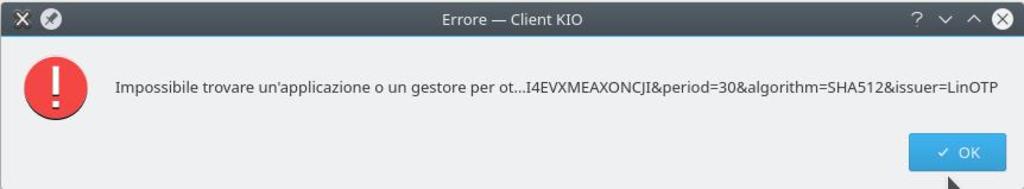
Then when clicking ok you get:
Impossible to find an application or a manager for … (the link).
So, no idea, no understanding. Do I miss an application, is this because of Opera, should I or shouldn’t I use the link???
I am totally lost, I find the procedure tedious, I find the information you can find on the web not intuitive, incomplete, confusing.
Is there anybody who managed this and knows how to do this on a Linux system?
Using opensuse Leap 15

Thanks in advance.