Maybe some Linux users do not yet know the Linux Vendor Firmware Service. However, it’s a great combined effort (as per this whitepaper also on the freedesktop.org site) to be able to update flashable devices in your devices, without having to boot Windows/Mac OS or so.
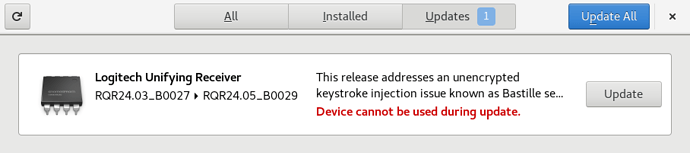
Well… in any case, what matters is that you get firmware updates on many Linux distros. Here e.g. with GNOME:
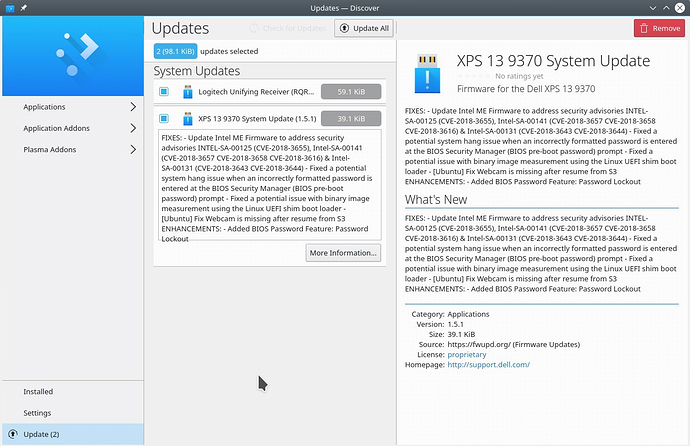
Or KDE:
More information for end users are here. (screenshots also taken from there)
If it all works, this would prevent the burden for Linux users to fiddle with the command line for updates as it is currently the case (instructions at the bottom of linked site), and would enable a secure one-click update for your Nitrokey (Storage) devices.
To get to the technical details, this whole thing depends on Nitrokey, of course. And, good news, actually they are already included in the vendor list on the site!
Bad news: They have not yet submitted any stable firmware updates there (last red column) and their statement there says:
The Nitrokey storage device should be supported soon
“Soon”?? ![]()
Note that actually one update for the “Nitrokey Storage” has been published (v0.50). However, there are some strange points about it:
-
On the site, it is listed as a “testing” update. Quote:
Warning: This firmware is in the testing state and may not be suitable for production systems.
However, the description of the update itself claims it is stable (highlighting by me):
This stable release fixes the following issues: […]
-
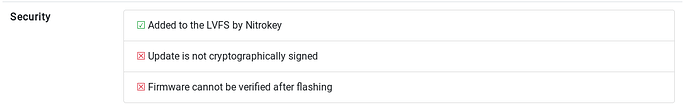
The security info at the bottom shows: “Update is not cryptographically signed” and “Firmware cannot be verified after flashing”.
This may not be a problem if the update is verified on the Nitrokey itself when applying. But an additional signature would not have been wrong. And it would have removed that pesky warning.
Even major other vendors like Dell are better at this and regularly upload firmware there. So I would have expected you to do better as a privacy-centric vendor, especially when you are being preferred by Linux users and even Linux kernel maintainers use your devices. ![]()
Note that 0.50 is also an outdated release as of the date when writing this post, so you should really get on that and deliver updates in this way.